Sorry, but I don’t know how else I can help you. I’ve just tried again the sample above. I’ve modified it for working with my company AD domain. I had an application.properties file like this one:
jmix.ldap.use-active-directory-configuration=true
jmix.ldap.user-search-filter=(&(objectClass=user)(sAMAccountName={1}))
jmix.ldap.active-directory-domain=mycompany.com
jmix.ldap.urls=ldaps://dc.mycompany.com:636/
jmix.ldap.base-dn=<some_base_dn>
jmix.ldap.manager-dn=<manager_dn>
jmix.ldap.manager-password=<manager_password>
BTW, did you set the jmix.ldap.active-directory-domain property? How do you enter the username on the login page: just “someuser” or “someuser@somedomain”?
When I authenticate with AD user, I see that execution comes to the com.company.demo.ldap.CustomAuthorityMapperBean#mapAuthorityToJmixRoleCodes
You may see the stacktrace (from which methods it was invoked) on my screenshot
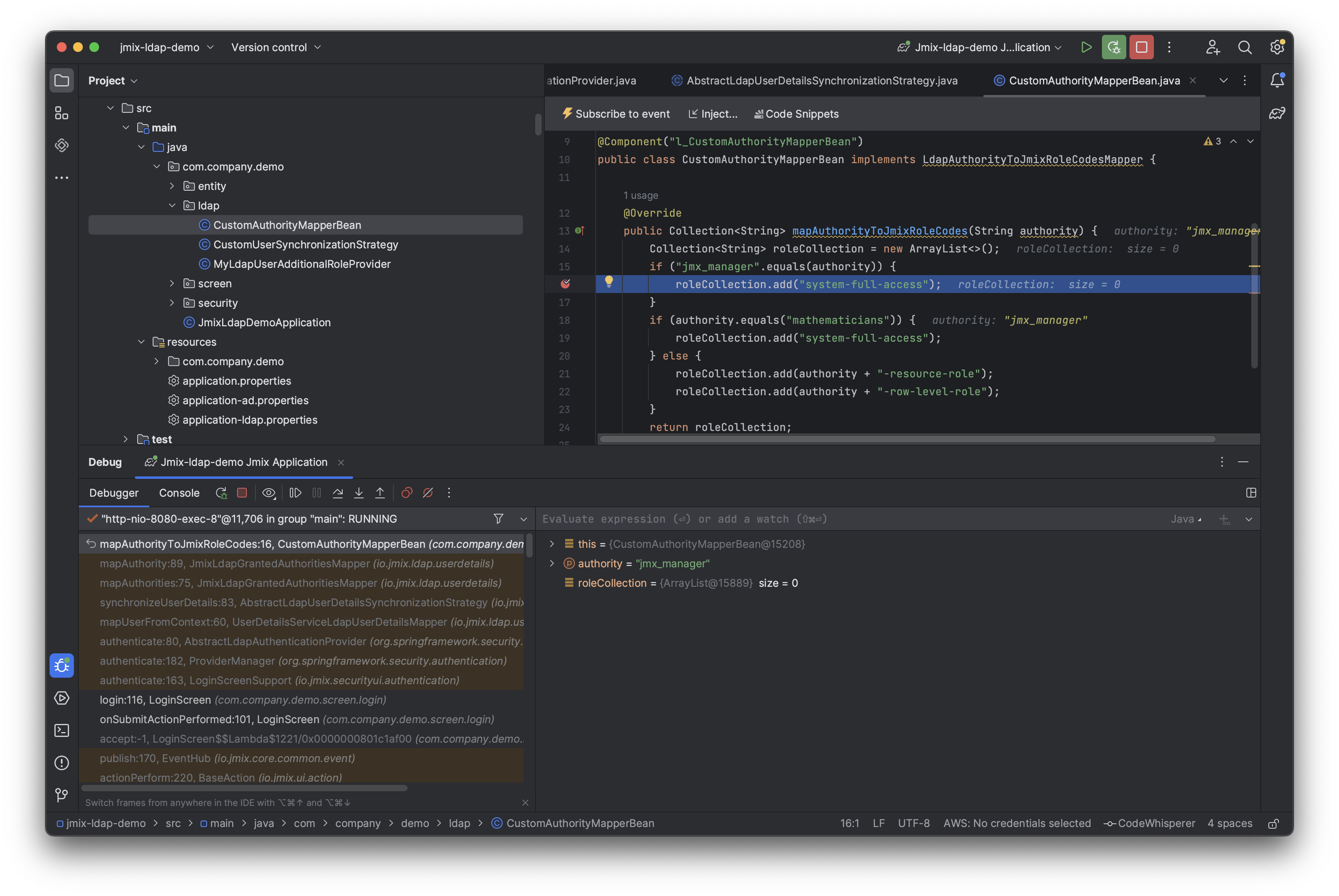
You can debug it on your side and try to find “the difference”.
The “authority” value there is a name of the user group in the AD (the memberOf attribute). By default group name is mapped to jmix role “as is”. You can always put a breakpoint in the io.jmix.ldap.userdetails.AbstractLdapUserDetailsSynchronizationStrategy#synchronizeUserDetails and see what happens.
Also, it seems that LdapUserAdditionalRoleProvider doesn’t work for AD authentication. I’ve created an issue for that.
