Hi,
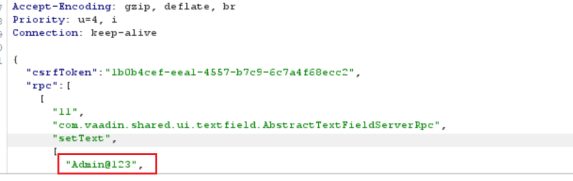
just to clarify: in any login flow — whether it’s a traditional form-based login (e.g., HTML + Spring Security), a React frontend calling a REST or OAuth endpoint, or a Vaadin-based UI — the password needs to be transmitted to a server at some point, typically when the user clicks the “Login” button.
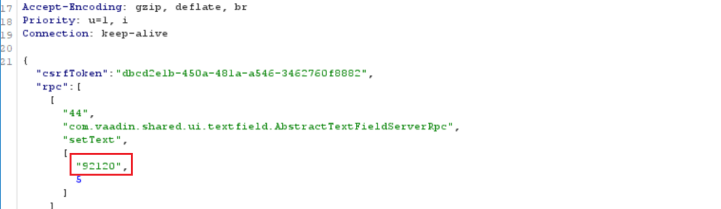
In Vaadin, depending on how components are configured, the client might send additional input events (like pressing Backspace) to the server, but that’s unrelated to the actual login process. Even without those interactions, the full password is always transmitted when the login is triggered.
The crucial part is that this transmission happens securely — and that’s why using HTTPS is essential. HTTPS ensures that the communication between browser and server is encrypted on the transport layer, so that sensitive data like passwords cannot be intercepted or read by third parties (e.g., on public Wi-Fi or corporate proxies).
Even when using OpenID Connect (OIDC), the password is still transmitted — not to your application, but to the identity provider (e.g., Keycloak, Google, etc.). So an HTTP-based interaction involving the password still takes place — just outside your app.
If you want to go a step further and avoid transmitting passwords altogether, some identity providers support WebAuthn, a browser standard for passwordless login based on asymmetric cryptography. With WebAuthn, authentication is performed using a private key stored securely on the user’s device (e.g., via Face ID, fingerprint, or a hardware token like YubiKey). Only a signed challenge is sent to the server — the password never leaves the device, and in fact, there is no password at all.
However, this also means adopting a different authentication paradigm: instead of identifying users by their credentials, the system identifies them based on registered public keys. So yes — it’s possible to avoid sending passwords, but it requires support for passwordless login and a proper public/private key infrastructure, either through something like WebAuthn or mutual TLS.
In short: if you’re using passwords (even with OIDC), they must be transmitted — securely. If you’re not using passwords at all (e.g., with WebAuthn), then transmission of secrets can be avoided entirely — but that also shifts the identity model and comes with different requirements.
Best regards,
Mario