Hi,
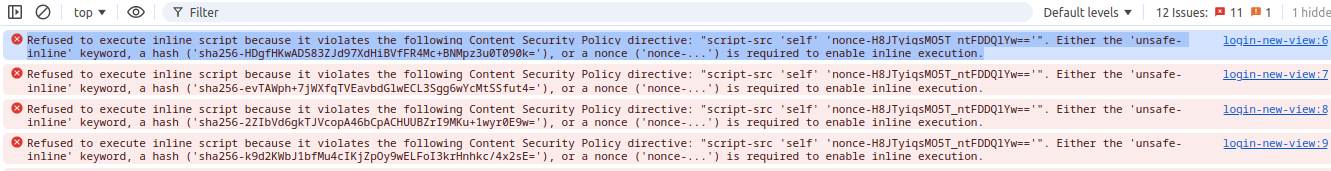
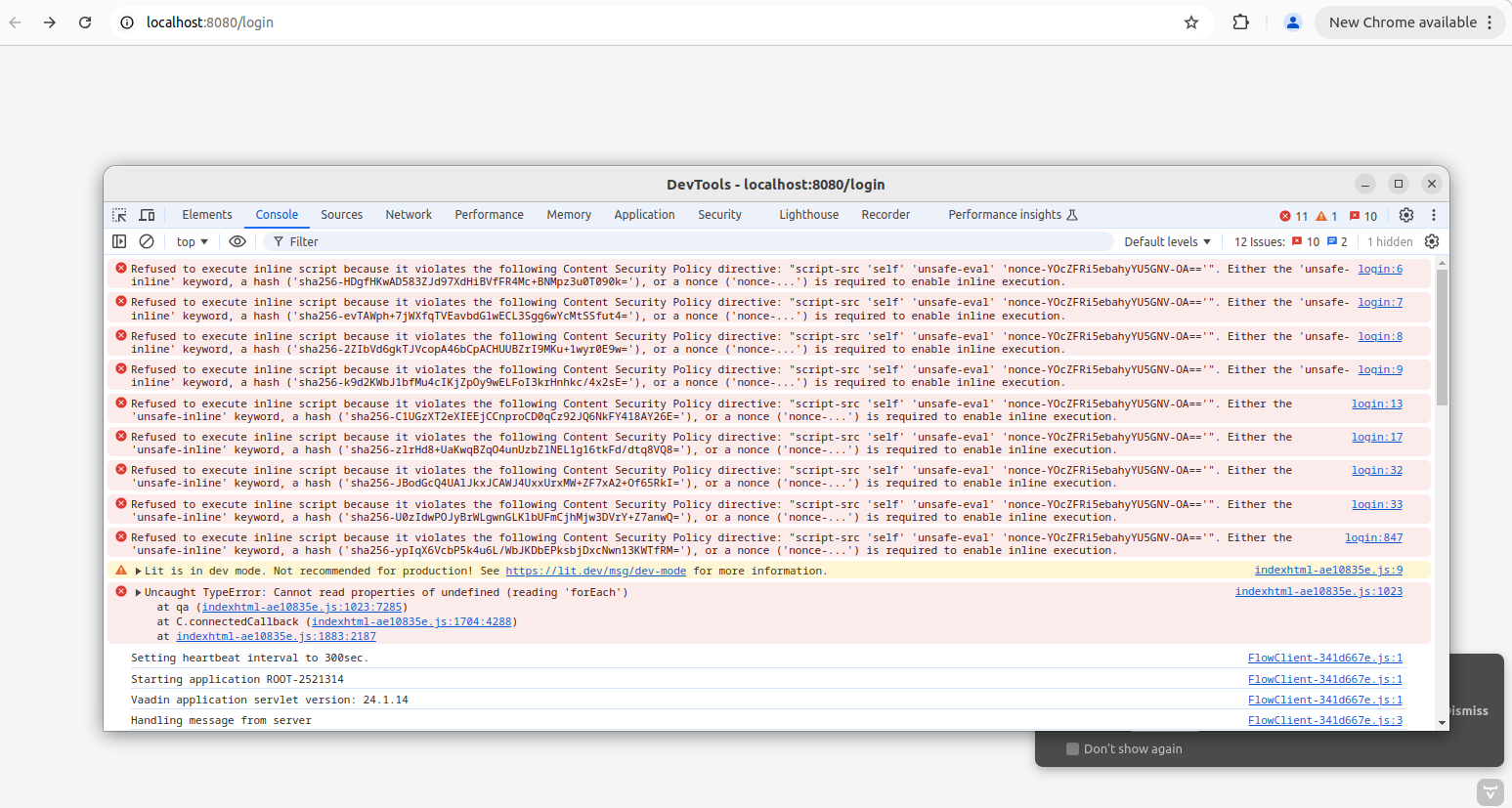
I have implemented below code but still changes are not working on browser
Jmix Verision : JMIX 2.1.3
public class HttpMethodFilter extends OncePerRequestFilter
{
byte[] nonceBytes = new byte[16];
secureRandom.nextBytes(nonceBytes);
String nonce = base64Encoder.encodeToString(nonceBytes);
// Set the nonce in the response header
HttpServletResponse httpServletResponse = (HttpServletResponse) response;
httpServletResponse.setHeader("Content-Security-Policy", "script-src 'self' 'nonce-" + nonce + "'");
// Pass the nonce to the request attributes for use in HTML
request.setAttribute("cspNonce", nonce);
}
–
LoginNewView.java
{
getUI().ifPresent(ui -> {
String cspNonce = (String) VaadinSession.getCurrent().getAttribute("cspNonce");
ui.getPage().executeJs(
"var script = document.createElement('script');" +
"script.setAttribute('nonce', '" + cspNonce + "');" +
"script.textContent = \"console.log('Custom script with nonce');\";" +
"document.head.appendChild(script);"
);
});
}