Hi,
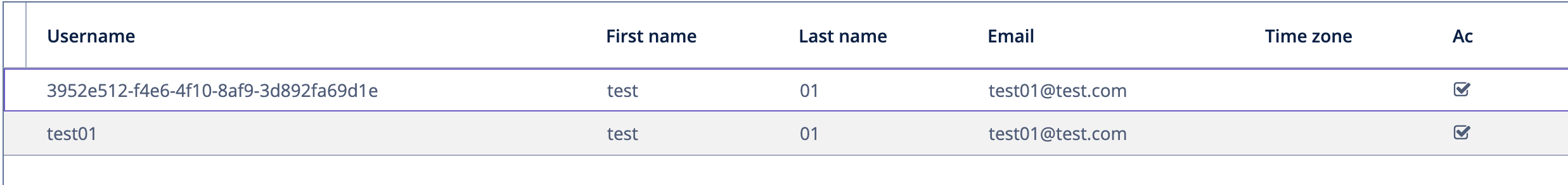
The problem is that different mechanisms are used for web login and for JWT bearer tokens.
The following application property says that the preffered_username claim will be used as Jmix user username:
spring.security.oauth2.client.provider.keycloak.user-name-attribute=preferred_username
For JWT access the “sub” claim is used as a username.
You have two options.
The first one is to remove the spring.security.oauth2.client.provider.keycloak.user-name-attribute application property, then the “sub” claim will be used as a username by default when you login by web.
The second option is to use the preferred_username claim as a username for JWT access. For this you’ll need to define and configure your own JmixJwtAuthenticationConverter that will replace the standard one.
@Bean
public JmixJwtAuthenticationConverter jmixJwtAuthenticationConverter(OidcUserMapper oidcUserMapper) {
JmixJwtAuthenticationConverter jmixJwtAuthenticationConverter = new JmixJwtAuthenticationConverter(oidcUserMapper);
jmixJwtAuthenticationConverter.setUsernameClaimName("preferred_username");
return jmixJwtAuthenticationConverter;
}
I’ve created in issue for this problem.