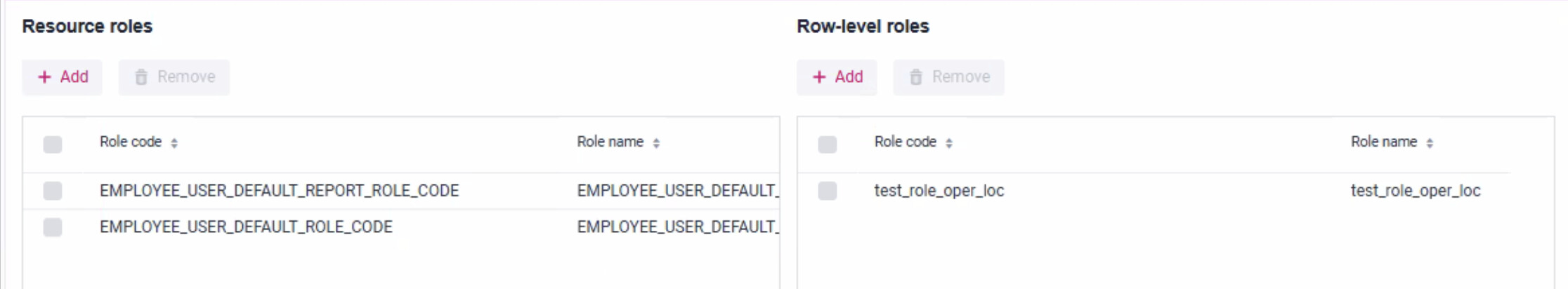
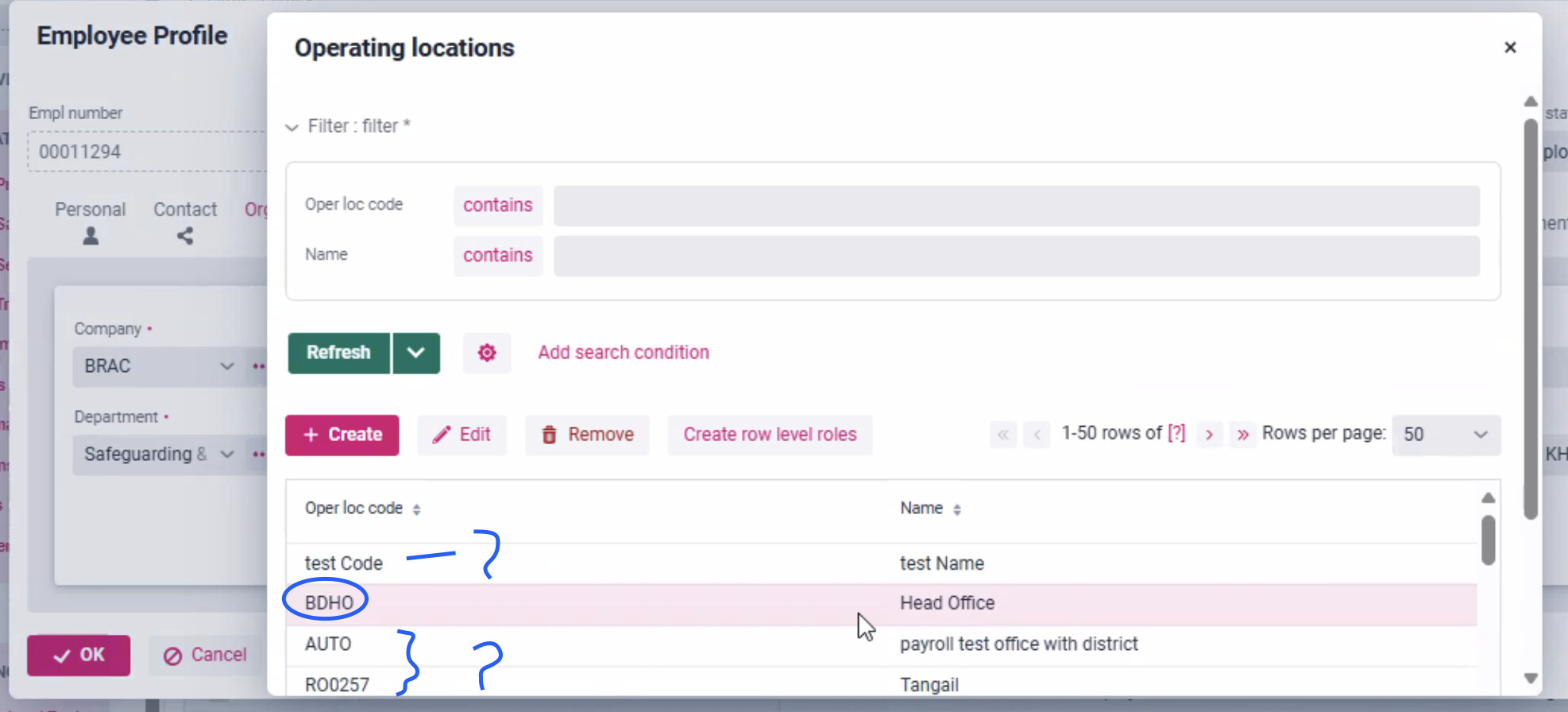
Thanks @f.zehnder
Hi @d.kremnev
Here is the SQL log
2025-05-18T17:48:18.997-04:00 DEBUG 57536 --- [nio-8080-exec-2] eclipselink.logging.sql : <t 1876172886, conn 363646483> [120 ms] spent
2025-05-18T17:48:18.999-04:00 DEBUG 57536 --- [nio-8080-exec-2] io.jmix.core.AccessLogger : Denied access to [entity 'mdg_OperatingLocation' create, update, delete] for user [13220723] by io.jmix.security.constraint.CrudEntityConstraint
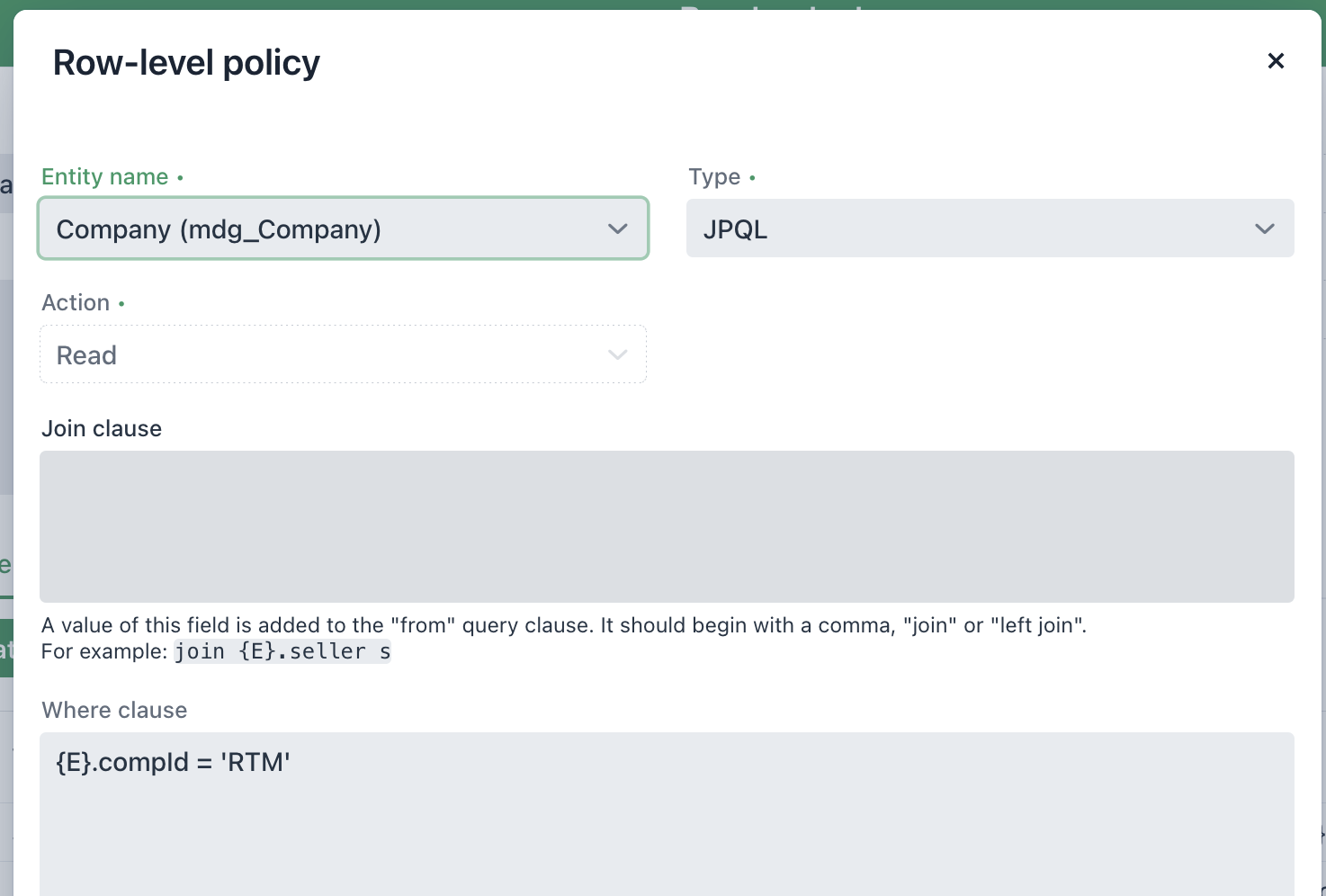
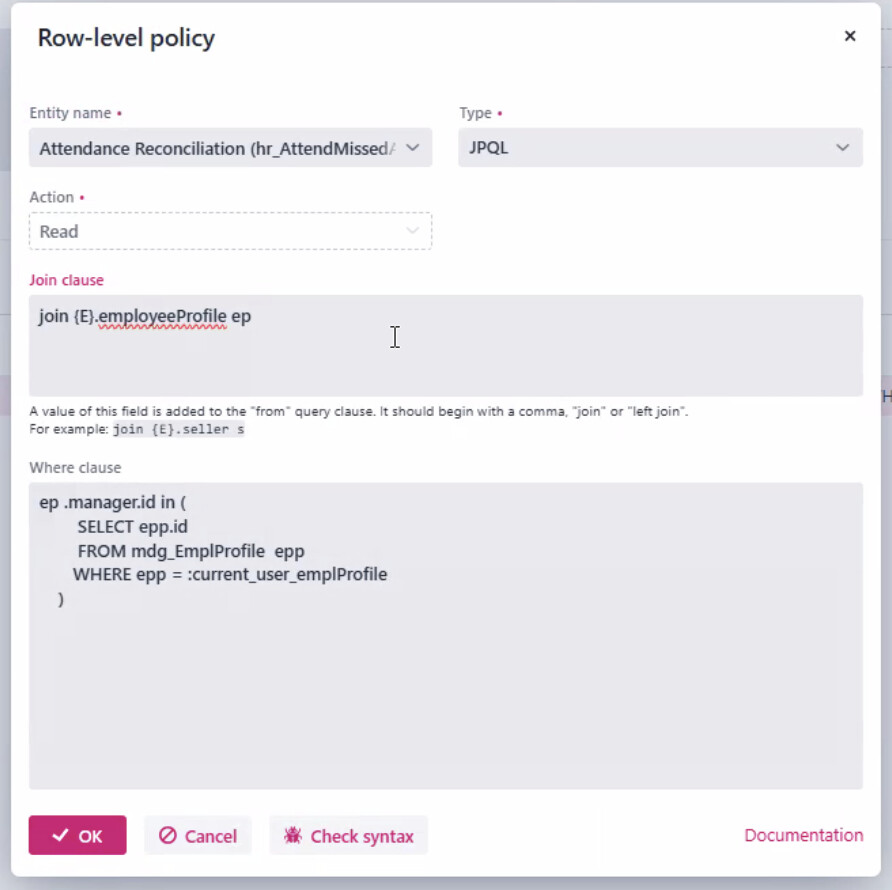
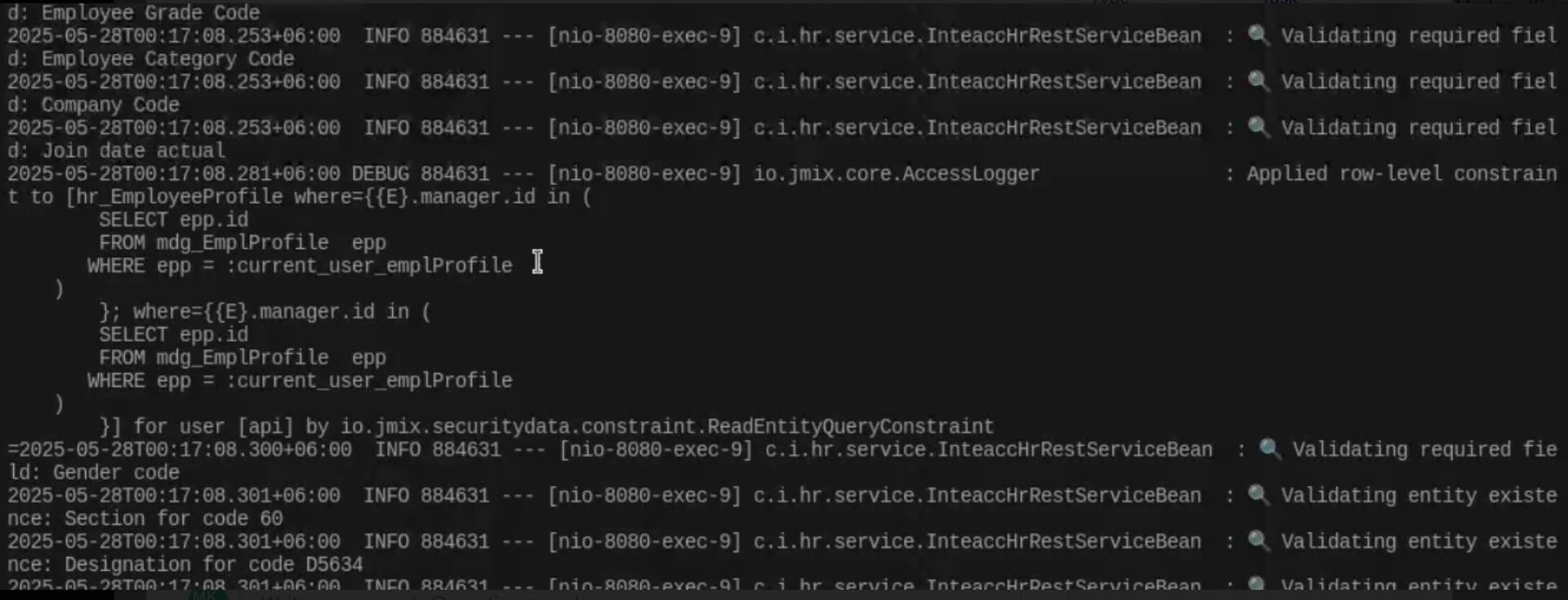
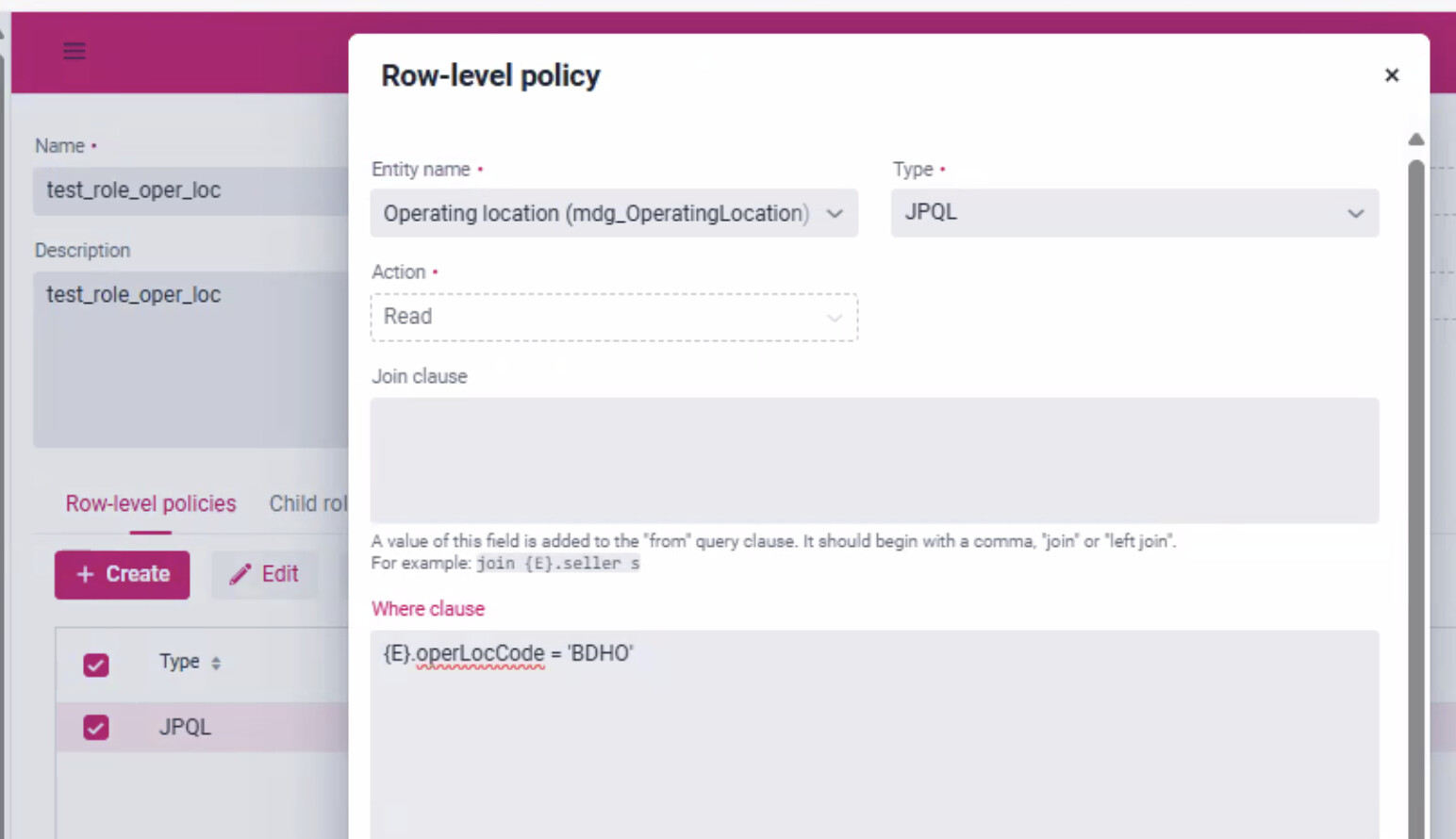
2025-05-18T17:48:19.000-04:00 DEBUG 57536 --- [nio-8080-exec-2] io.jmix.core.AccessLogger : Applied row-level constraint to [mdg_OperatingLocation where={{E}.operLocCode = '200' }] for user [13220723] by io.jmix.securitydata.constraint.ReadEntityQueryConstraint
2025-05-18T17:48:19.001-04:00 DEBUG 57536 --- [nio-8080-exec-2] eclipselink.logging.sql : <t 1876172886, conn 1456112828> SELECT ID, ADDRESS, ADDRESS_LOCAL, NAME, NAME_LOCAL, OPER_LOC_CODE, ROW_LEVEL_ROLE, USE_HOLI_CAL_DEFAULT_TO_EMPL, HOLIDAY_CALENDAR_ID, UPAZILA_ID, WORK_SHIFT_DEFAULT_ID FROM MDG_OPERATING_LOCATION WHERE (OPER_LOC_CODE = ?)
bind => [200]
2025-05-18T17:48:19.129-04:00 DEBUG 57536 --- [nio-8080-exec-2] eclipselink.logging.sql : <t 1876172886, conn 1456112828> [128 ms] spent
2025-05-18T17:48:19.130-04:00 INFO 57536 --- [nio-8080-exec-2] c.i.h.v.l.a.AttendMissedAppListView : Authorized company IDs: [2d54b78b-a90a-a3d9-1268-f676390c21f7]
2025-05-18T17:48:19.130-04:00 INFO 57536 --- [nio-8080-exec-2] c.i.h.v.l.a.AttendMissedAppListView : Authorized location IDs: [1ce30500-3d45-68da-39a5-2348f2f89a7a]
2025-05-18T17:48:19.131-04:00 DEBUG 57536 --- [nio-8080-exec-2] io.jmix.core.AccessLogger : Denied access to [entity 'hr_AttendMissedApp' delete] for user [13220723] by io.jmix.security.constraint.CrudEntityConstraint
2025-05-18T17:48:19.134-04:00 DEBUG 57536 --- [nio-8080-exec-2] eclipselink.logging.sql : <t 1876172886, conn 1681296009> SELECT t1.ID, t1.APPL_DATE, t1.ATTEN_DATE, t1.ATTEN_MISS_ENTRY_NO, t1.EMPL_ID_MACHINE, t1.IN_TIME, t1.OUT_TIME, t1.PROCESS_STATE, t1.VERSION, t1.EMPLOYEE_PROFILE_ID, t1.WORK_SHIFT_ID, t0.ID, t0.DTYPE, t0.EMPLOYEE_CODE, t0.FIRST_NAME, t0.LAST_NAME, t0.MIDDLE_NAME, t0.VERSION, t0.COMPANY_ID, t0.DEPARTMENT_ID, t0.DPS_MEMBER_ID, t0.FUNCTIONAL_AREA_ID, t0.GRATUITY_MEMBER_ID, t0.HR_BUSINESS_PART_PROF_ID, t0.JOB_FAMILY_ID, t0.MANAGER_ID, t0.MANAGER_MATRIX_ID, t0.MARKET_HIERARCHY_ID, t0.OPERATING_LOCATION_ID, t0.PF_MEMBER_ID, t0.WORKFLOW_GROUP_ID, t0.DELETED_BY, t0.DELETED_DATE, t0.ALLOWANCE_SECOND_PMT_ID, t0.ATTEND_LOCATION_ID, t0.BANK_BRANCH_ID, t0.CURRENT_COUNTRY_ID, t0.CURRENT_DISTRICT_ID, t0.DESIGNATION_ID, t0.EMPL_CATEGORY_ID, t0.EMPL_GRADE_ID, t0.EMPL_GRADE_SUB_ID, t0.EMPL_SEPARATION_ID, t0.EMPLOYEE_GROUP_ID, t0.HOLIDAY_CALENDAR_ID, t0.HR_BUSINESS_PARTNER_ID, t0.JOB_POSITION_ID, t0.JOB_PROFILE_ID, t0.LEAVE_PROFILE_ID, t0.NATIONALITY_ID, t0.PAYSCALE_ID, t0.PAYSCALE_CMP_ID, t0.PAYSCALE_STRUCTURE_ID, t0.PERMANENT_COUNTRY_ID, t0.PERMANENT_DISTRICT_ID, t0.PR_PAYMENT_METHOD_ID, t0.PR_PAYMENT_METHOD_SEC_ID, t0.RELIGION_ID, t0.SECTION_ID, t0.WORK_SHIFT_ID, t0.WORK_SHIFT_ROTATE_RULE_ID, t2.ID, t2.CODE, t2.CREATED_BY, t2.CREATED_DATE, t2.LAST_MODIFIED_BY, t2.LAST_MODIFIED_DATE, t2.NAME, t2.VERSION, t3.ID, t3.NAME, t3.OPER_LOC_CODE, t3.HOLIDAY_CALENDAR_ID, t3.UPAZILA_ID, t3.WORK_SHIFT_DEFAULT_ID, t4.ID, t4.NAME, t4.SHIFT_CODE, t4.VERSION, t4.OT_ROUNDING_RULE_ID, t4.PUNCTUAL_ATTEND_CRITERIA_ID FROM HR_ATTEND_MISSED_APP t1 LEFT OUTER JOIN MDG_EMPL_PROFILE t0 ON (t0.ID = t1.EMPLOYEE_PROFILE_ID) LEFT OUTER JOIN HMD_DESIGNATION t2 ON (t2.ID = t0.DESIGNATION_ID) LEFT OUTER JOIN MDG_OPERATING_LOCATION t3 ON (t3.ID = t0.OPERATING_LOCATION_ID) LEFT OUTER JOIN MDG_WORK_SHIFT t4 ON (t4.ID = t1.WORK_SHIFT_ID) ORDER BY ROW_NUMBER() OVER (ORDER BY (SELECT null)) OFFSET ? ROWS FETCH NEXT ? ROWS ONLY
bind => [0, 50]