Supposed we have generate the access Auth2 token for user A but if I pass same access token for user B it is valid and give the response this should not be happen in this case what need to do for this?
Hello!
Can you provide more details? Which Jmix version do you use, how do you configured Auth configuration?
It would be great to have demo project that represent this error. Btw seems like critical security issue but in which side - Jmix or yours - I can’t say without details.
Best regards,
Dmitry
I using Jmix version 2.4.3 Rest API project
my Auth2 configuration will share demo application soon
The client id
spring.security.oauth2.authorizationserver.client.myclient.registration.client-id=abc
The client secret
spring.security.oauth2.authorizationserver.client.myclient.registration.client-secret={noop}Abc@123
Enable Client Credential grant for the my-client
spring.security.oauth2.authorizationserver.client.myclient.registration.authorization-grant-types=client_credentials, password
Client credentials must be passed in the Authorization header using the HTTP Basic authentication scheme
spring.security.oauth2.authorizationserver.client.myclient.registration.client-authentication_methods=client_secret_basic
Use opaque tokens instead of JWT
spring.security.oauth2.authorizationserver.client.myclient.token.access-token-format=reference
spring.security.oauth2.authorizationserver.client.myclient.token.access-token-time-to-live=24h
For eg. Supposed I have send auth 2 request with user admin I getting the access token from
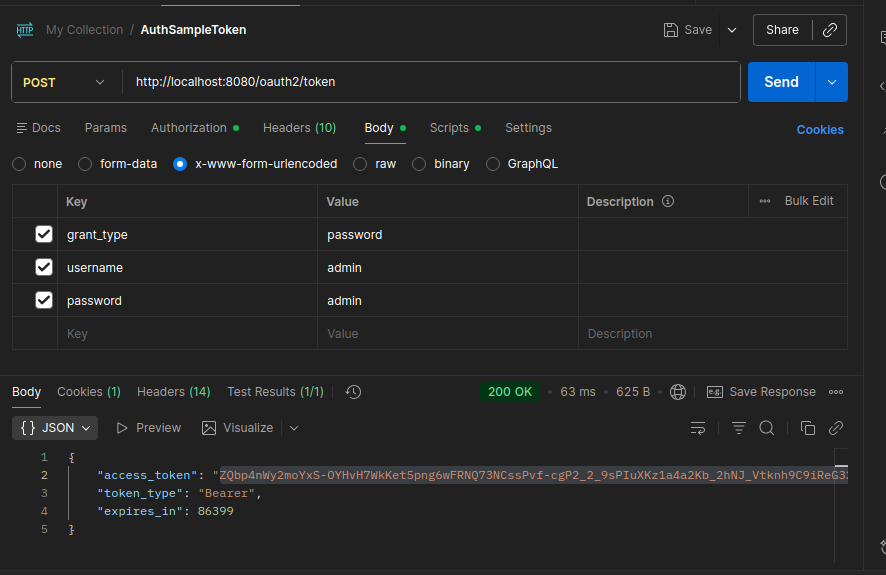
But after that I have send one more auth 2 request which is send by user krish
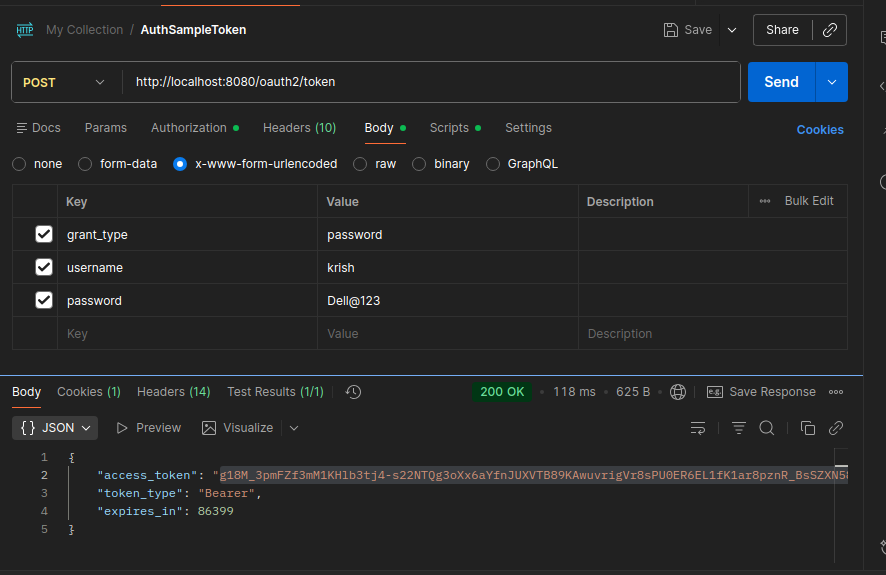
and I used this access token and try to access my api it will giving valid response
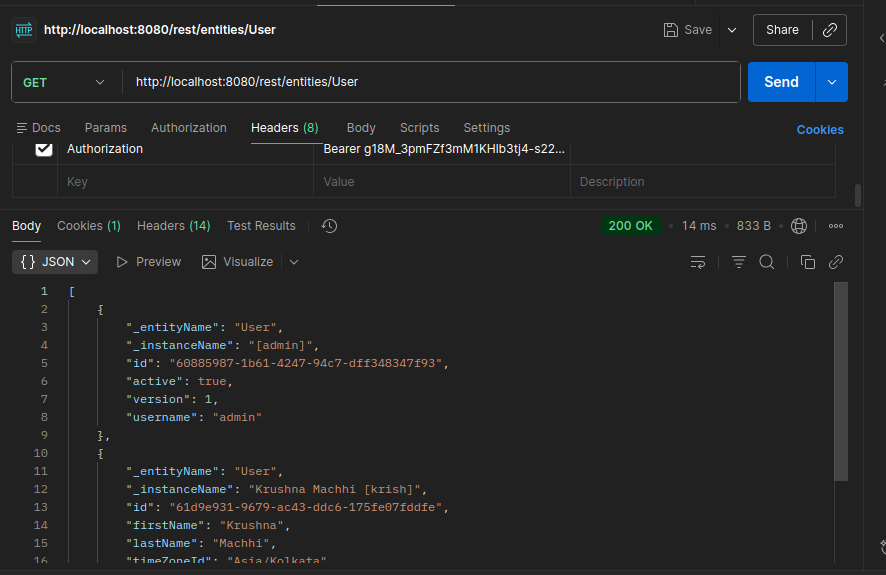
How can I understand which access token is for which user. For otp generation case I want to allow only that perticuler user access token only that user can get the otp if in between someone can change the access token then it should return the response unauthorize access
You are using Password Grant and have got 2 tokens: first for user admin, second for user krish.
Then you used the second token to access the API. So your request on the last screenshot was executed from user krish.
What’s the problem?
But in OTP Generation scenarios I am generating otp for admin user and sending token in the request of user krish still otp is getting generated
Same user token can allowed to access there api. If we generate token for other user and send this token with another user request then it should be give unauthorize access error
How you know this is executed for user krish the attacker is changing the access token
As I understand, you want to disallow basic users to get access int generic rest api. This feature can be implemented by roles not by token. You can read more about tokens, jwts and other stuff about how fields(lik ein jwt) puts “json” into token, fields and how tracks it in spring docs - jmix here just providing spring auth, and as i understand you, this is a common behaviour.
e.g. for jwt you can contain roles, nickname etc in its field:
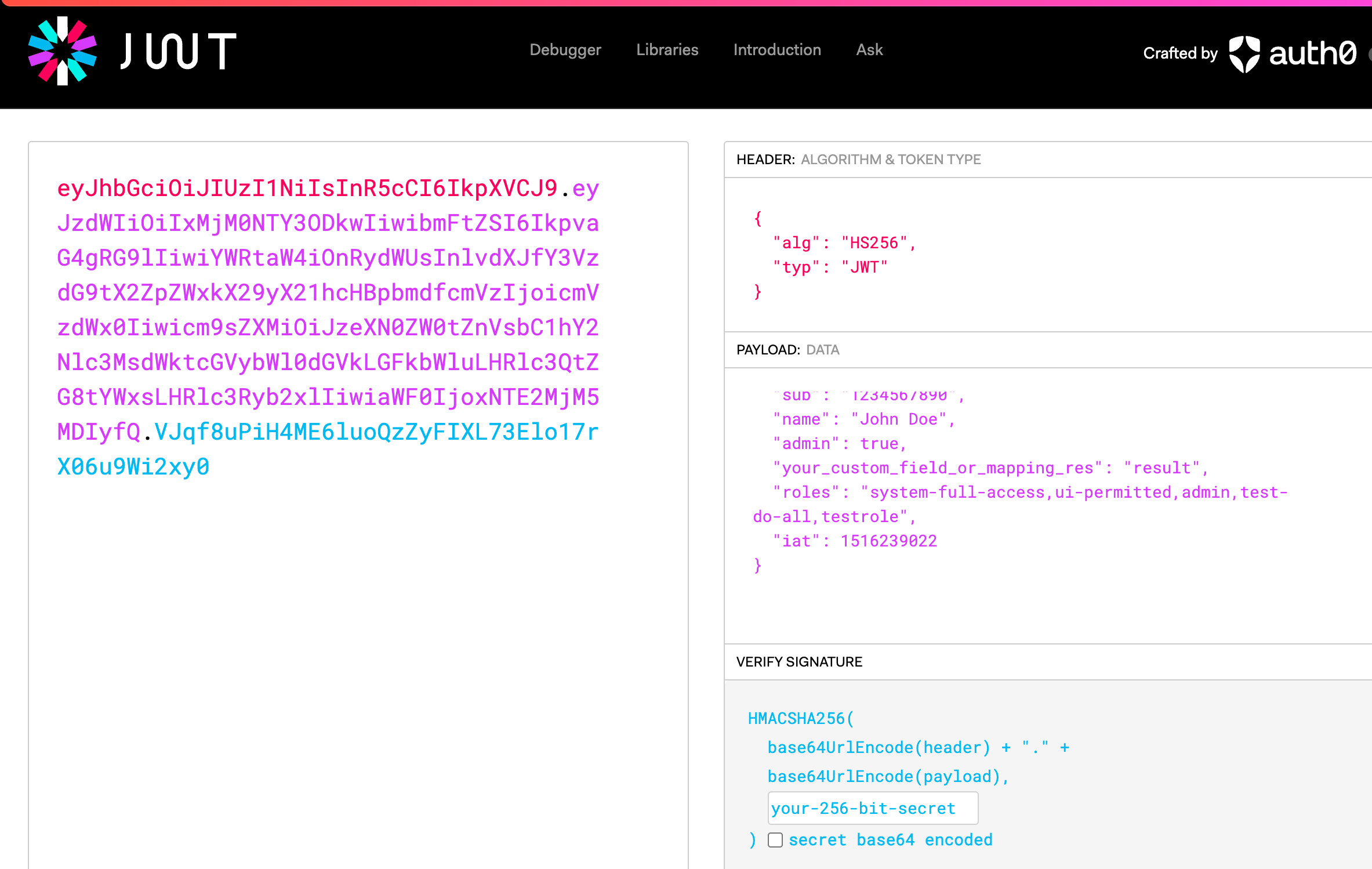
Im not sure about basic auth token has same encoding, but idea is same. Btw in token we can track some fields, constants.
If you talking about that common user with rest access can find admin user - generic rest is ADMIN and system level API that never should be exposed to common users - only internal systems. If you want to let user check api - create own spring controller, annotate it @Role or other spring security annotations to avoid unauthorized requests… But we are not filtering content by roles.
So, as i understand you x2, the problem is not about token but about permission and accessing management, roles and etc.
Best regards,
Dmitry
Access token has a user login encrypted inside. Having access token is absolutely sufficient to to access the system under the user this token has been issued for.
Stealing an access token is like stealing a user’s password.
Passing an access token to another user is like passing your password to another user (that is: one must never do this).
See e.g. this explanation:
for OAuth2 - whoever has a valid access_token would have access to resources designated by that token. For how long depends on OAuth2 the implementation of provider.
it is arguably more important that access tokens are kept confidential. Therefore the API provider should ensure that access tokens, which in OAuth2 are also known as Bearer tokens, are valid only for as short time as possible. These tokens work like passwords, and if intercepted can be used immediately by an attacker.