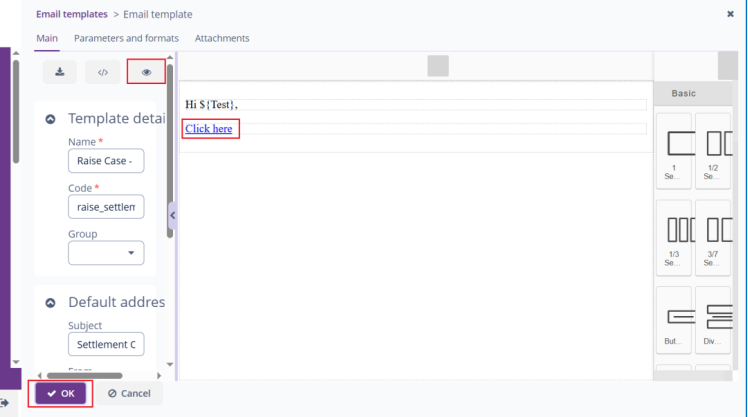
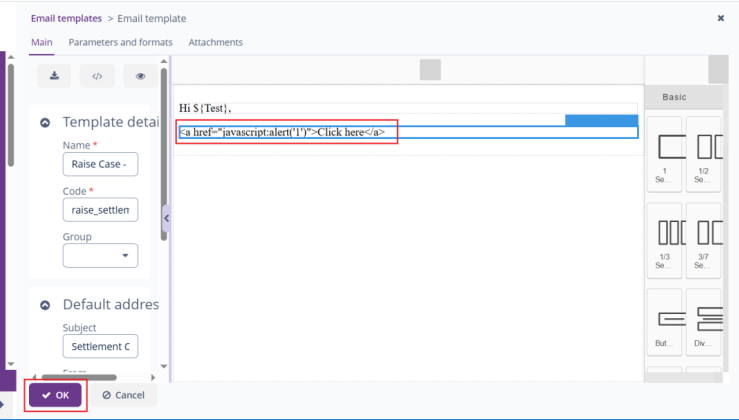
Hello,
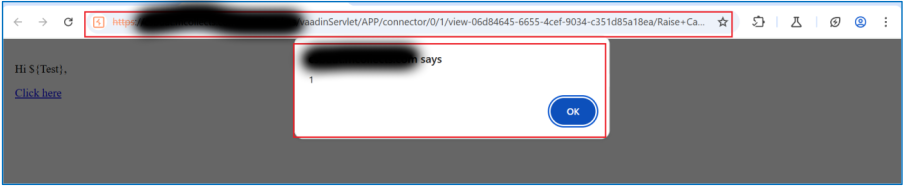
Thank you for reporting a problem! I tried to reproduce your case, but javascript is not executed in the editor. Could you clarify where this is executed?
The result HTML is saved in JsonEmailTemplate entity. It contains the html property. You can check it in onPreCommit method. Or you can override the component to get/set already sanitized values. For instance:
ExtGrapesJsNewsletterHtmlEditorImpl.class
public class ExtGrapesJsNewsletterHtmlEditorImpl extends GrapesJsNewsletterHtmlEditorImpl {
@Override
public String getValue() {
String value = super.getValue();
return sanitize(value);
}
@Override
public void setValue(String value) {
String sanitized = sanitize(value);
super.setValue(sanitized);
}
}
And component registration:
@Bean
public ComponentRegistration extGrapesJsNewsletterHtmlEditorImpl() {
return ComponentRegistrationBuilder.create(GrapesJsNewsletterHtmlEditor.NAME)
.withComponentClass(ExtGrapesJsNewsletterHtmlEditorImpl.class)
.withComponentLoaderClass(GrapesJsNewsletterHtmlEditorLoader.class)
.build();
}
Pay attention that you should check how the default sanitizer will work with template parameters.
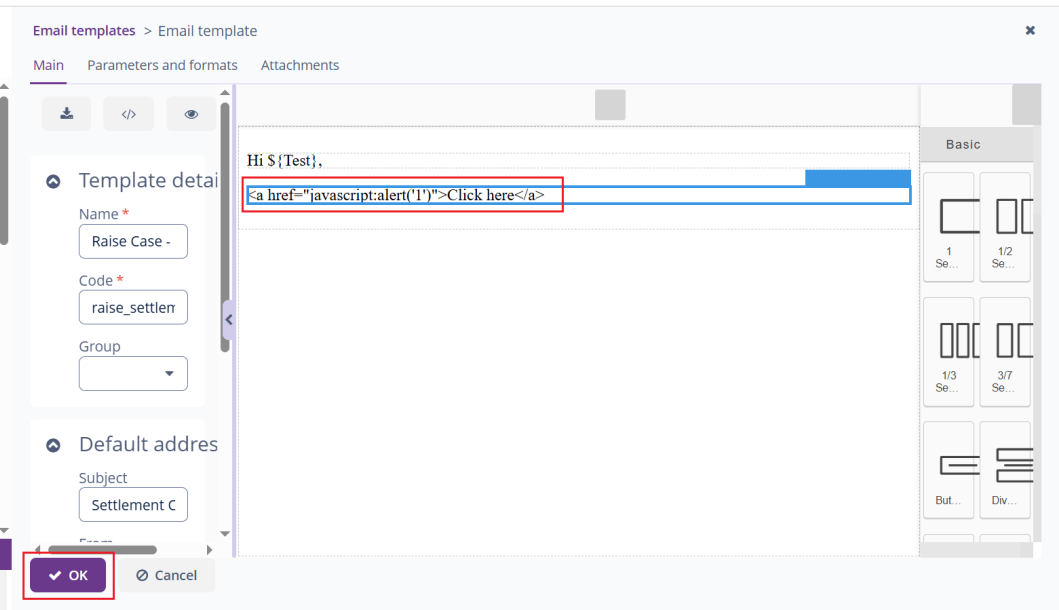
![]()