I discovered that the users password is presented in plain text when running REST call agains Jmix.
This information should be encrypted and also be hidden from REST by default.
Hi,
All information transferred over the REST is encrypted on the transport level - using the HTTPS mechanism (SSL / TLS). No additional encryption of passwords is required, it doesn’t make much sense.
What do you mean by “hidden from REST” ? Do you mean client_id / client_secret used in the oauth/token request?
Exposing a password can be risky.
The password on the server should not be sent to the client for comparison.
Rather the opposite, comparison on server. Just a suggestion?
Server knows the password but not client. Then it should be natural to check passwords on the server side and not on the client side. Again just a suggestion?
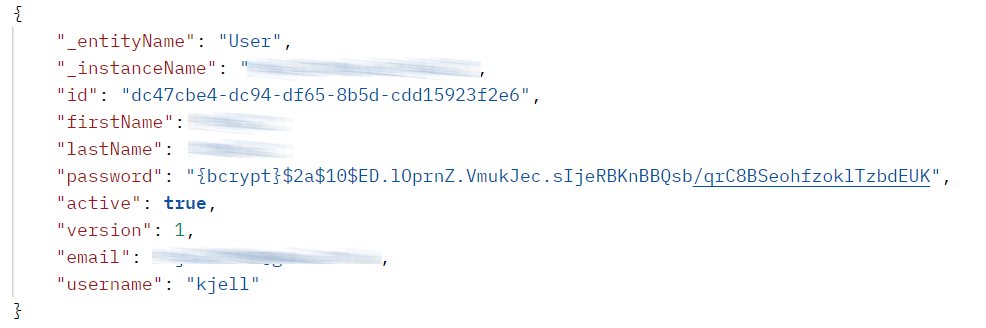
Could you be more specific please?
When exposing a pasword?
During which operation the password is sent to the client for comparison now?
I’m sorry but you’re just not giving enough context.
FYI during the oauth login - the password of course is checked on the server side, it’s not sent to the client. Not sure when you got that JSON answer, probably the user was already logged in.
Just forget it. I discovered that I was thinking wrong here 