Hi,
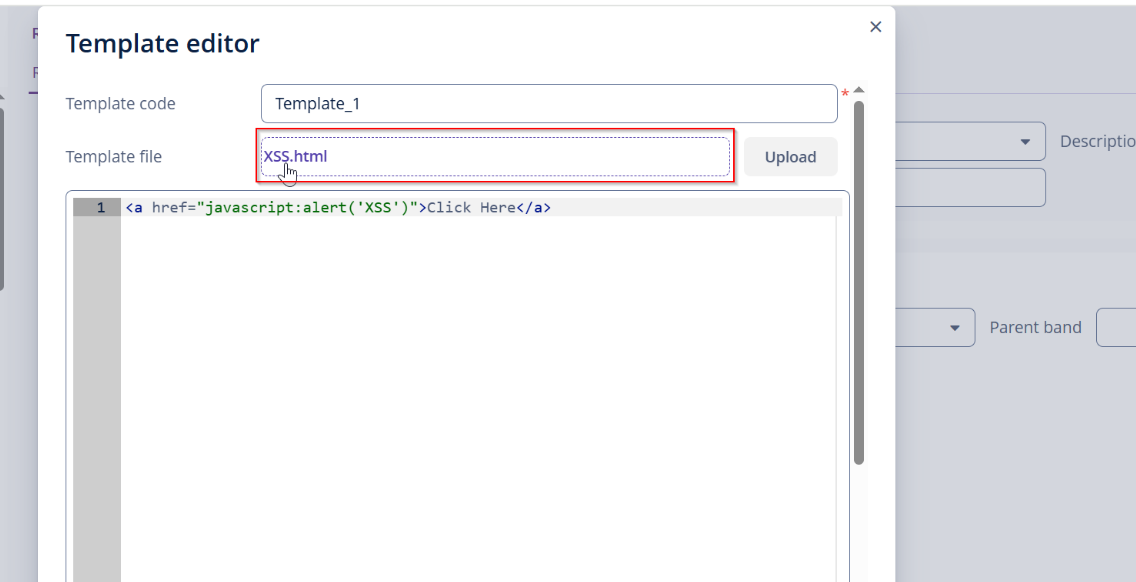
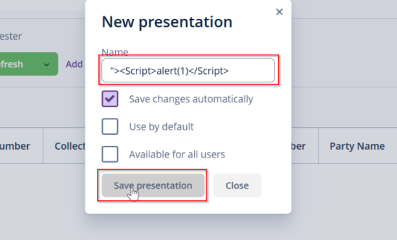
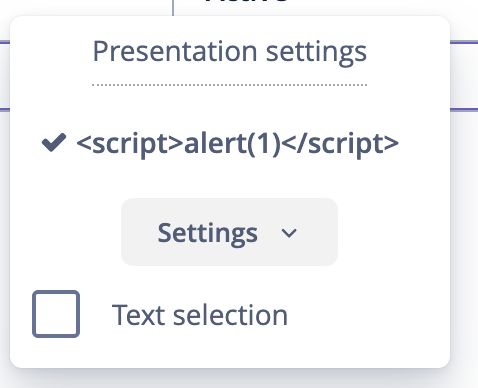
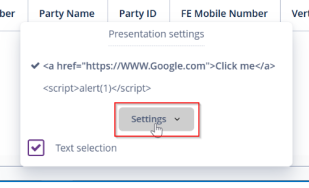
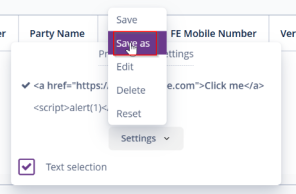
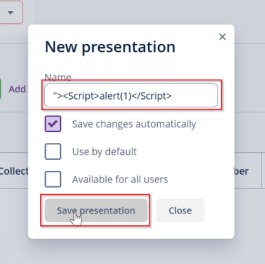
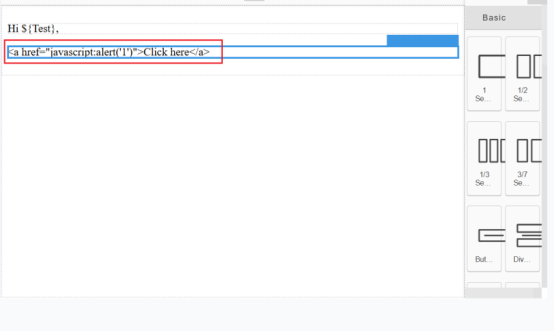
This vulnerability occurs when a web application allows users to upload files without proper
validation or sanitization, leading to the execution of malicious scripts. In this scenario, you
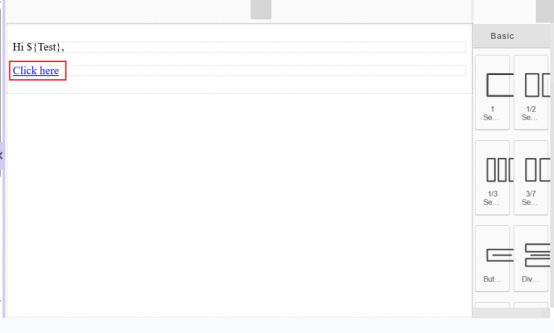
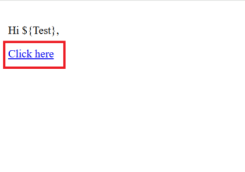
uploaded a file containing an XSS payload, and when clicking on the file name, the JavaScript
executed successfully, confirming the vulnerability. If exploited, an attacker can execute
arbitrary scripts in the context of a victim’s session, potentially leading to session hijacking,
phishing, or further attacks.
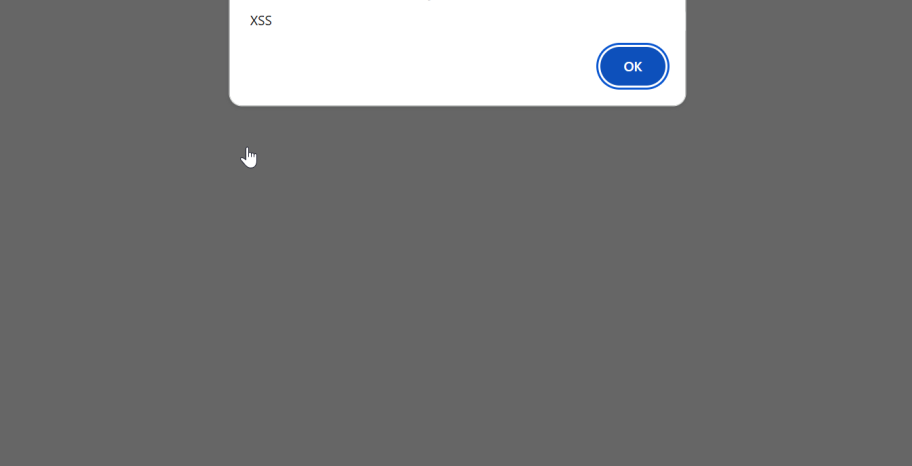
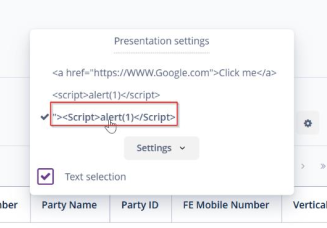
The XSS alert popup message was successfully displayed.